With the release of the Windows 10 1903 update, a new feature was introduced and that is the Windows 10 Sandbox. Microsoft have a blog post detailing the details of it. But in summary this sandbox is not typically like a VM. It acts more like an application, you can even pin it to your taskbar!

Also all changes to the sandbox are lost when it is closed. This would include any new software installed to it, as well as any OS and/or application configuration changes made to it. This is big from a security tool perspective, since it allows for a quick and easy environment to perform some security based research.
Reasearch VMs
There are times when we need to open a page or install an application which we are not too sure about. And once we've done so we would like to research it, to determine if it is malicious, and if so research it further to determine the motives, attack style, threat actors, etc. Typically in the past a way of doing this would involve using a virtual machine (VM) run on a hypervisor such as VirtualBox or VMWare Workstation Player/VMWare Workstation Pro. One would create a base image of the VM and then take a snapshot of the VM. Only then would the VM be run and appropriate site visited or application installed. Once the researcher had finished their research, they would power down the VM and then restore the snapshot. Not only this, the researcher would need to keep the snapshot up to date with the latest OS and application patches. While not a tremendous amount of work, it does add a bit of overhead.
Windows Sandbox
There's a lot of clever technology going on behind the scenes to make the overall experience with the Windows Sandbox a lot more seemless. The blog post from Microsoft goes into a lot more details about this, so I recommend that you read that if you are interested in the lower level details. Suffice to say that now a lot of the overhead of maintaining a VM are no longer. The Sandbox makes use of a copy of the Windows installed on your machine, so this should mean that it will get the updates automatically. Also as mentioned previously, when the sandbox is closed it effectively wiped and restored to it's original state. This is extremely useful when performing research on potentially malicious software. It provides a clean state every time the sandbox is opened from new. The one draw back however is that one is not able to save a state, so this could be an issue if you perform a longer term research project. For this, you will likely need to stick with a more traditional VM.
Sandbox With a Proxy
One of the reasons to use the sandbox is to browse potentially malicious sites and researching the traffic. In order to do this, you would require a proxy to intercept the requests. Using a proxy such as BurpStuite is possible with the sandbox using the following steps:
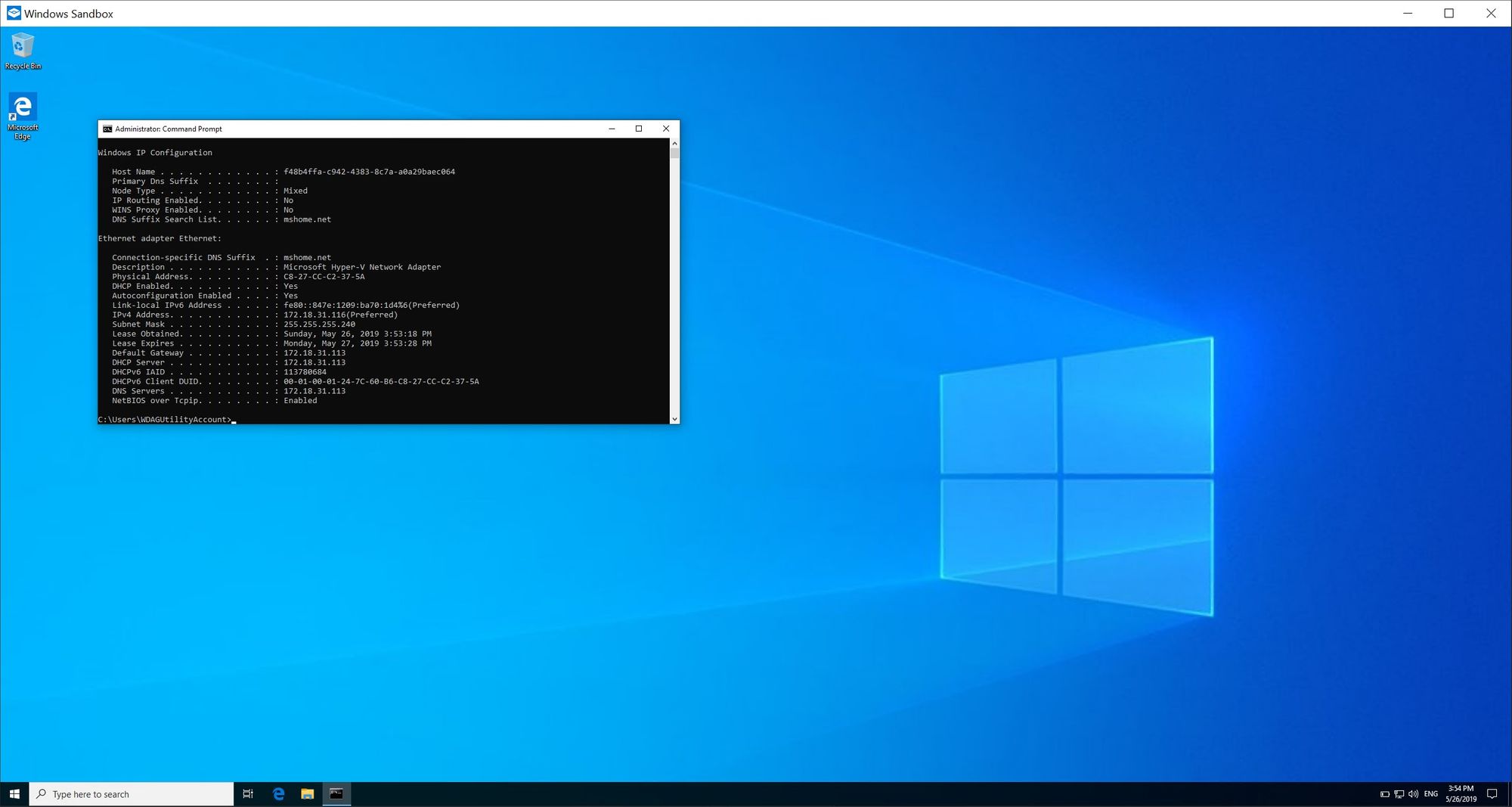
1. In the sandbox open the command prompt and run the following command:
ipconfig /all
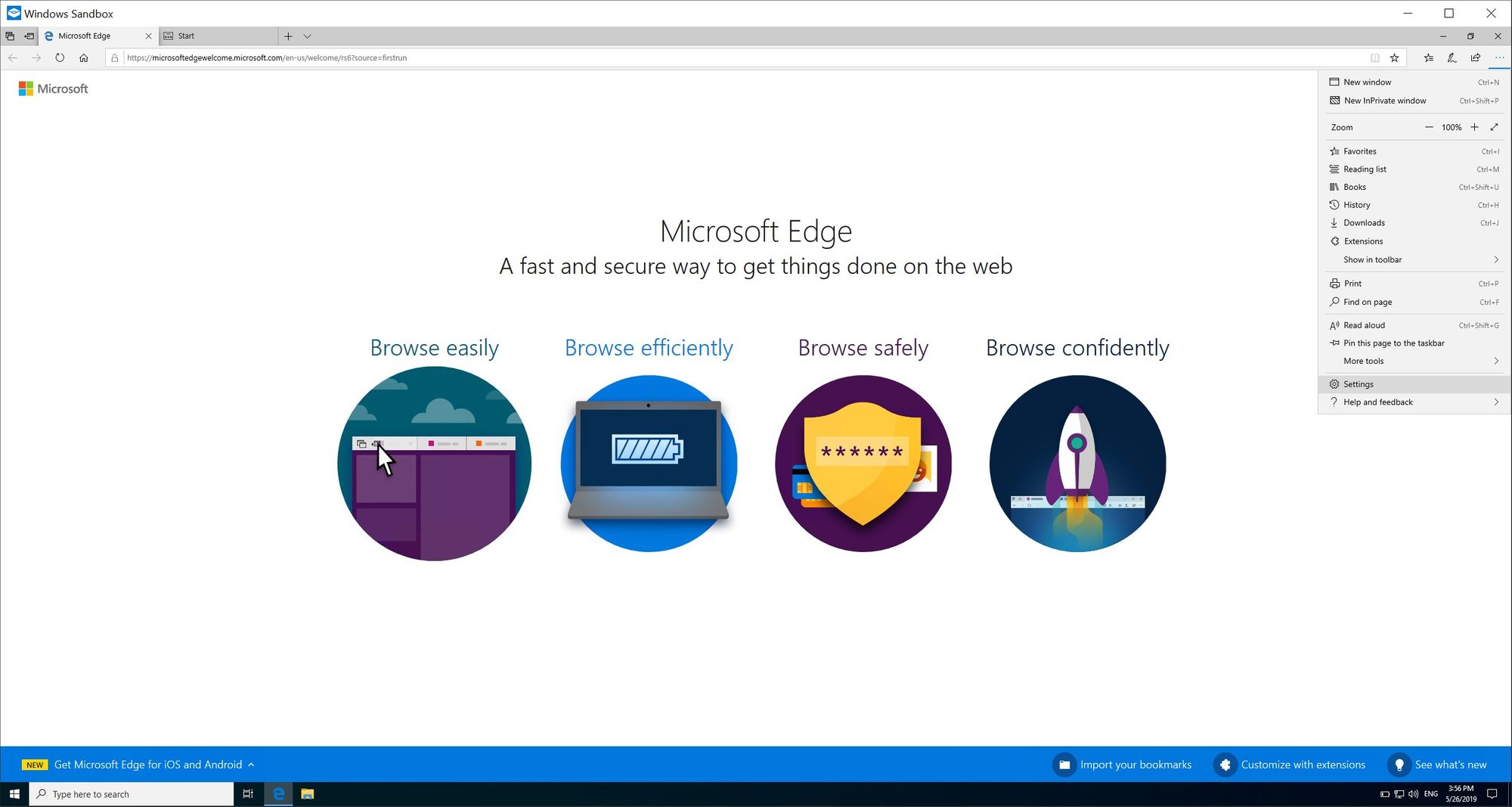
2. Open Edge in the sandbox and go to the Settings option:
3. Next select Advanced and then select Open proxy settings:
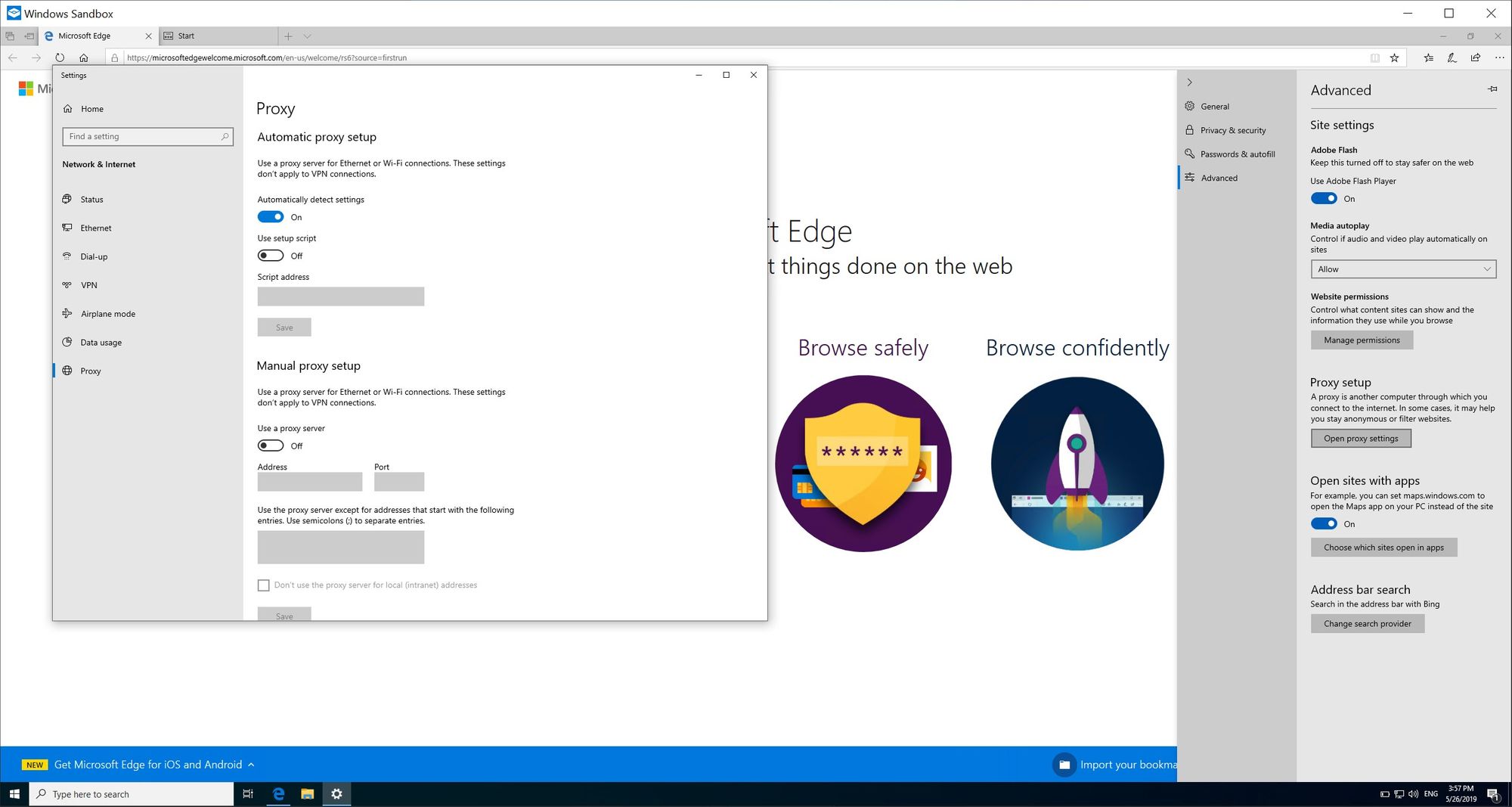
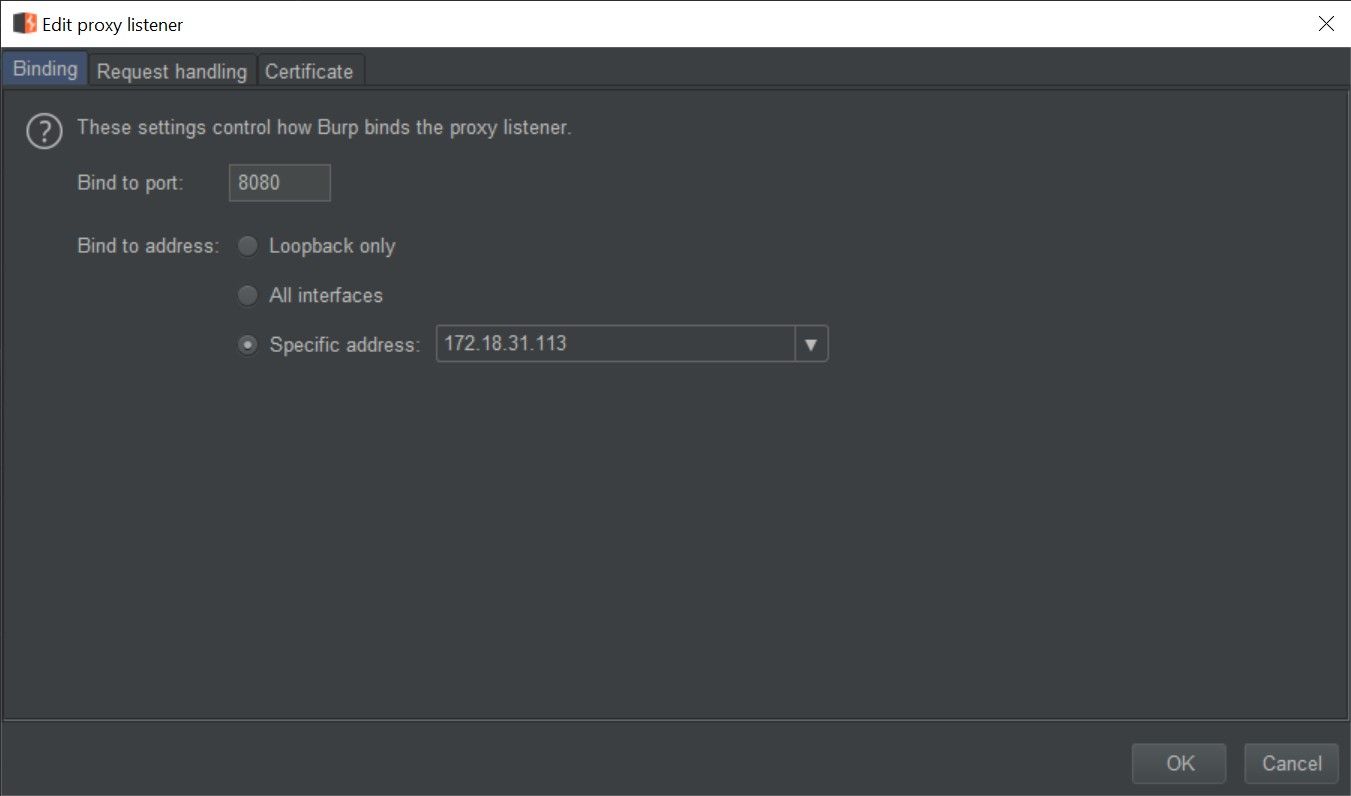
4. Open your proxy (in this example BurpSuite) and configure your proxy to listen on the IP which is the gateway for your sandbox (you can get this IP from the command prompt executed in the first step:
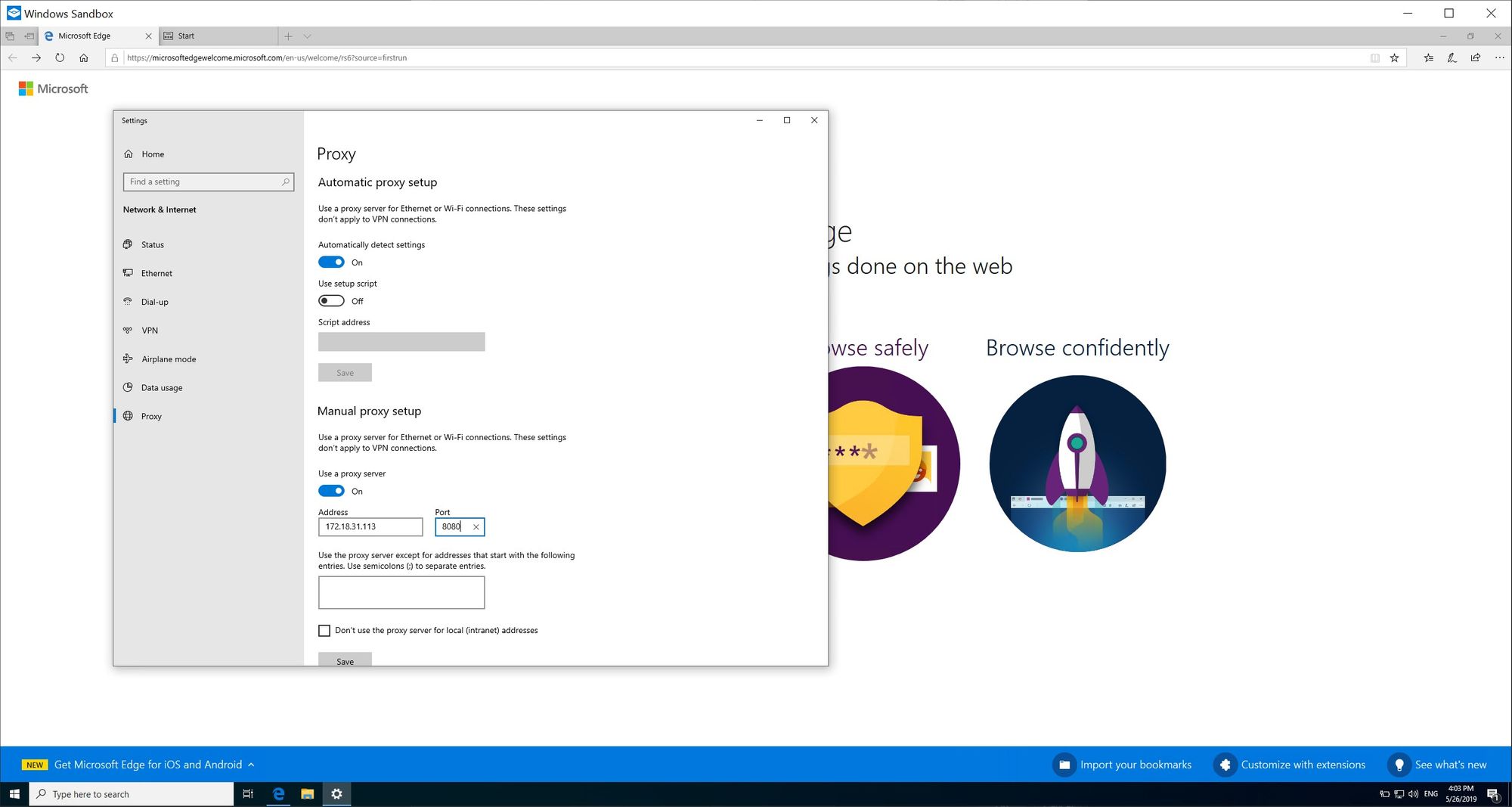
5. Back in your sandbox, configure your proxy (using the sandbox gateway IP as the IP of your proxy:
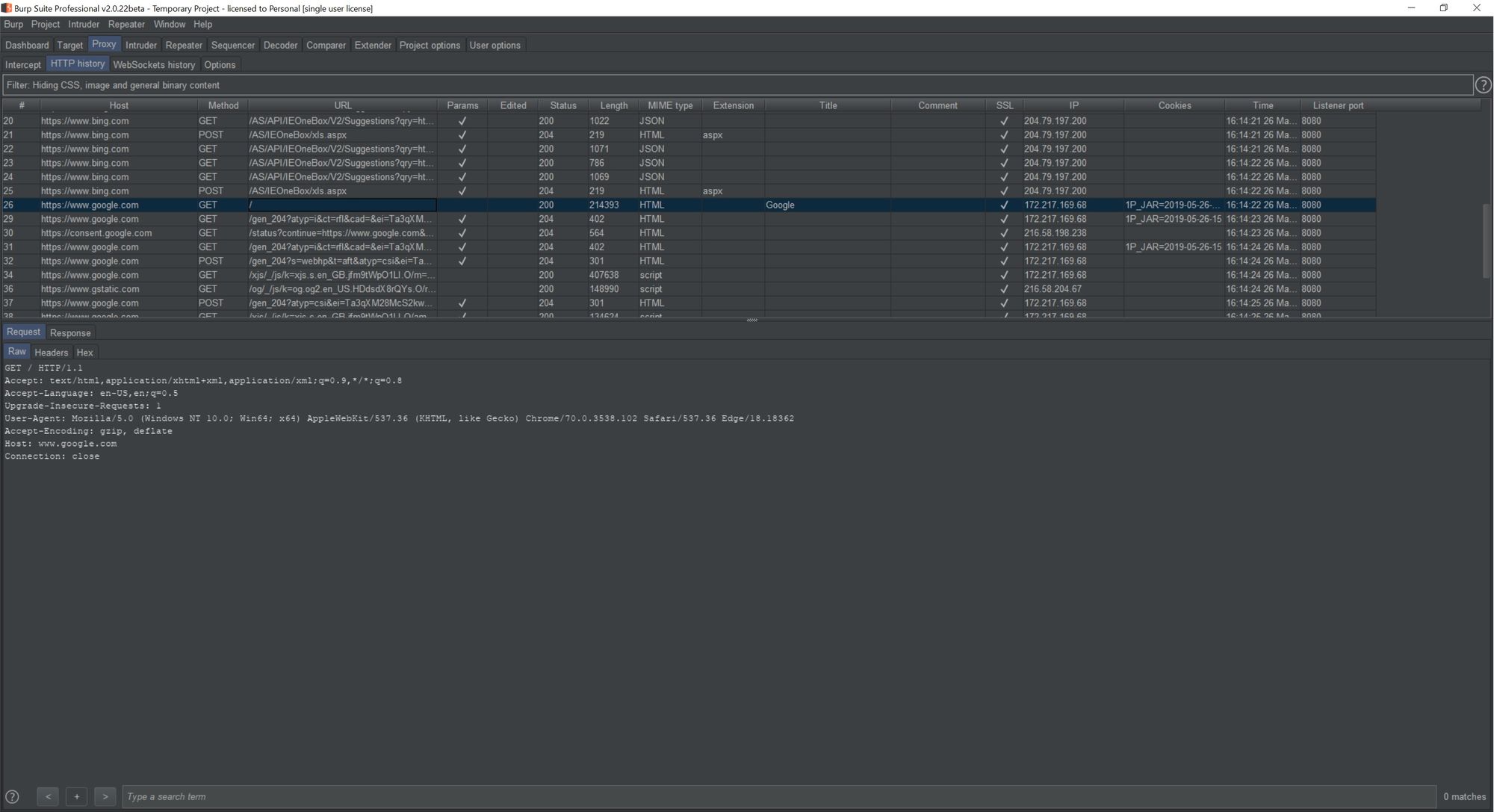
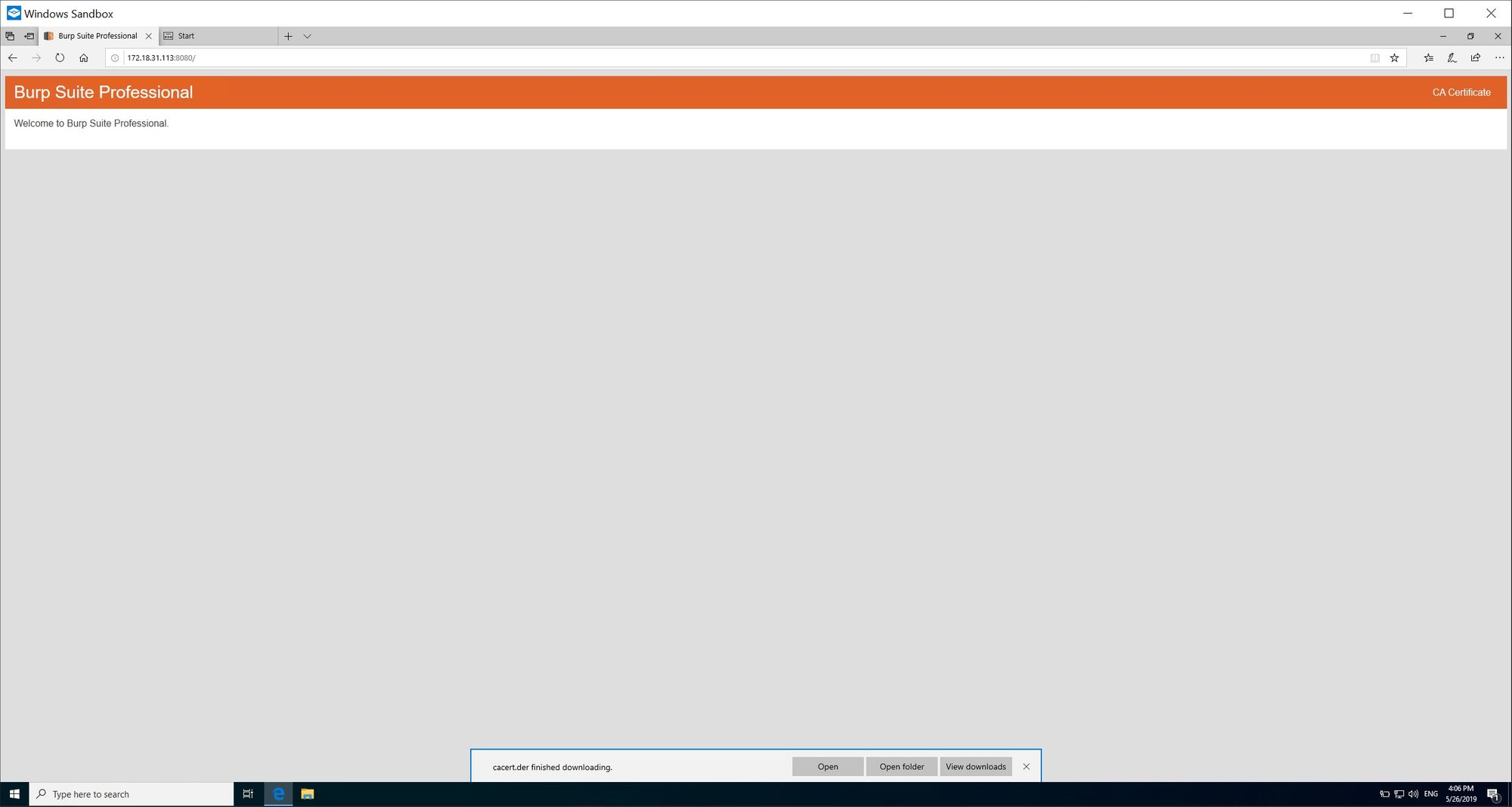
6. Obtain the CA certificate from your proxy (using BurpSuite you can obtain this from browsing to the proxy itself):
7. Open Internet Options (can be done by typing internet options in to search field on the taskbar):
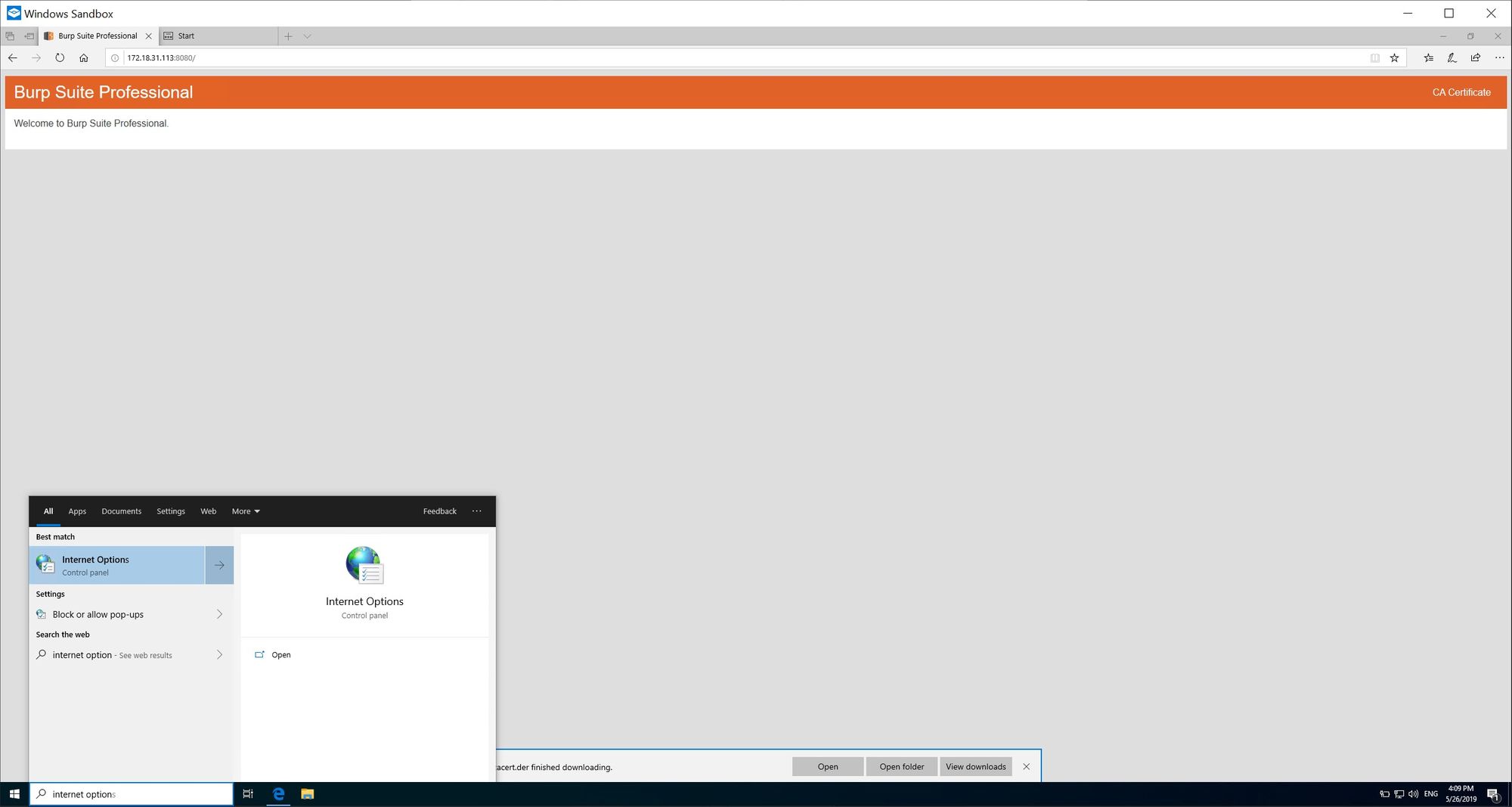
8. Go to the Content tab and then select Certificates:
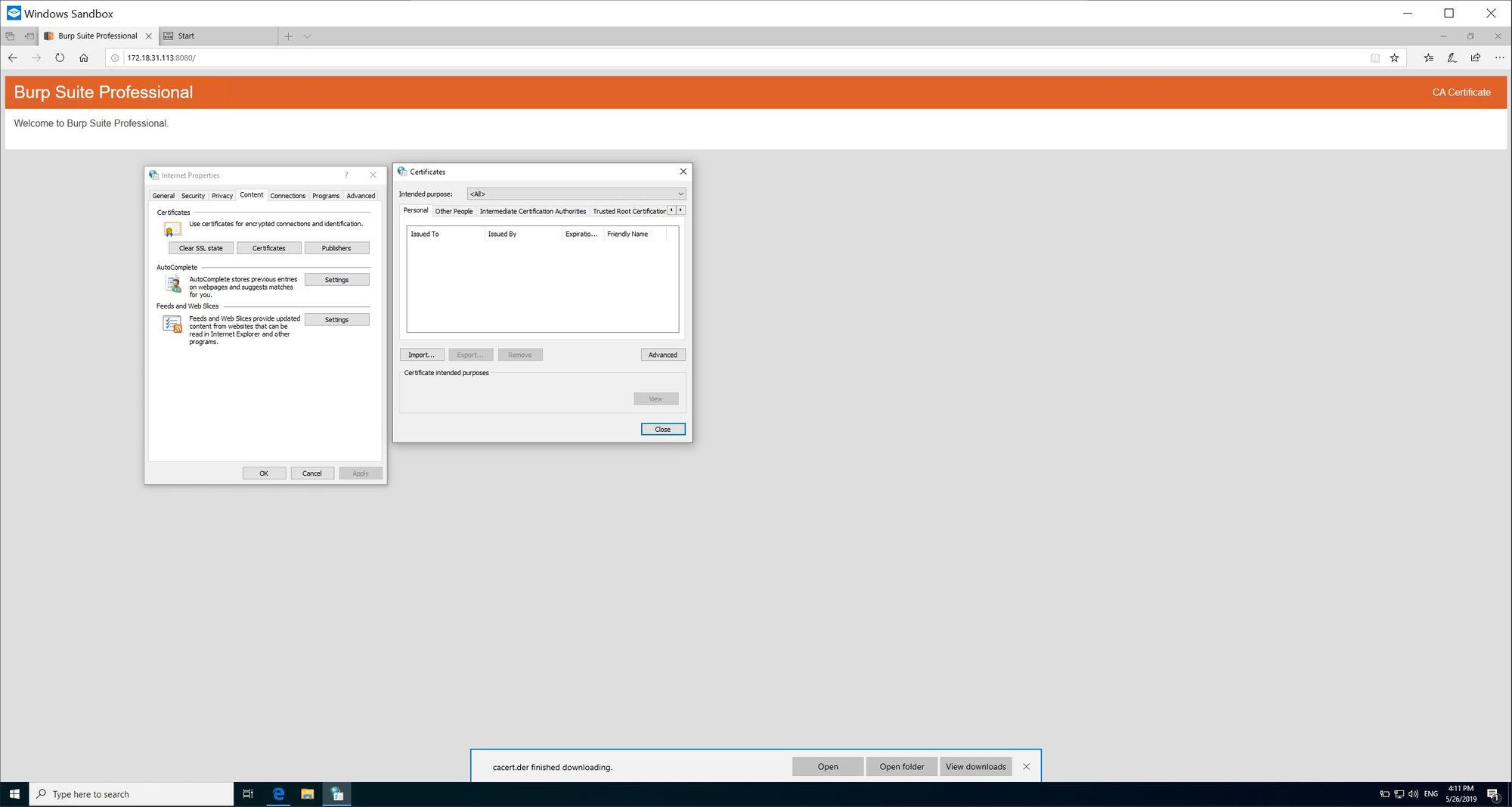
9. Select the Trusted Root Certification Authorities tab and import the downloaded proxy CA:
10. Confirm that the traffic is hitting your proxy: